Take manual snapshots and restore in a different domain spanning across various Regions and accounts in Amazon OpenSearch Service
AWS Big Data
OCTOBER 11, 2024
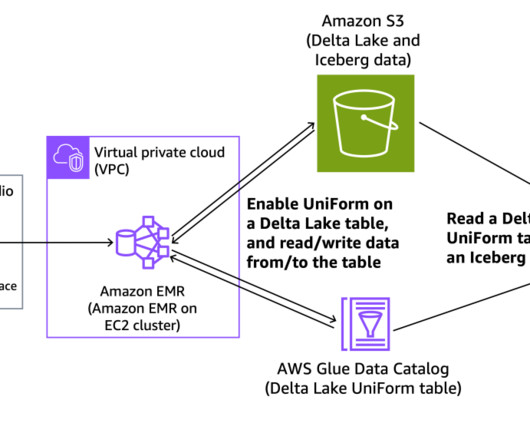
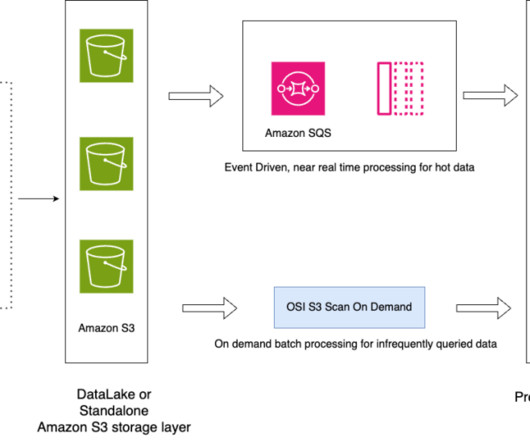
By implementing a robust snapshot strategy, you can mitigate risks associated with data loss, streamline disaster recovery processes and maintain compliance with data management best practices. Snapshots play a critical role in providing the availability, integrity and ability to recover data in OpenSearch Service domains.















































Let's personalize your content