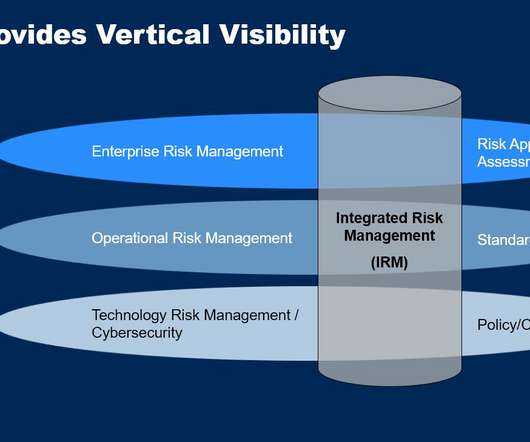
The Alignment Problem Is Not New
O'Reilly on Data
JUNE 15, 2023
Science fiction writer Charlie Stross has noted that today’s corporations can be thought of as “ slow AIs.” And much as Bostrom feared, we have given them an overriding command: to increase corporate profits and shareholder value. Attempts to add environmental, social, and governance (ESG) constraints have had only limited impact.
















































Let's personalize your content