How resilient CIOs future-proof to mitigate risks
CIO Business Intelligence
DECEMBER 18, 2024
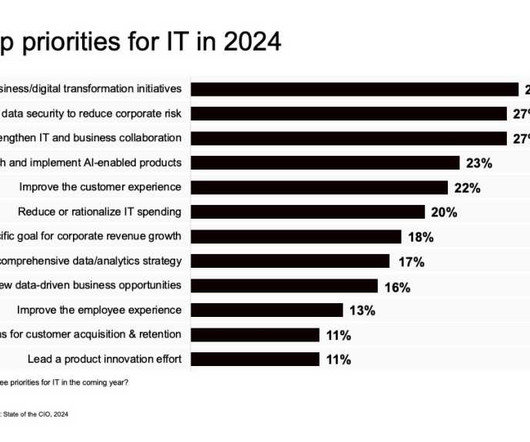
This year saw emerging risks posed by AI , disastrous outages like the CrowdStrike incident , and surmounting software supply chain frailties , as well as the risk of cyberattacks and quantum computing breaking todays most advanced encryption algorithms. Of these, AI is at the top of many CIOs minds.


















































Let's personalize your content