Automating Model Risk Compliance: Model Monitoring
DataRobot Blog
JUNE 27, 2022
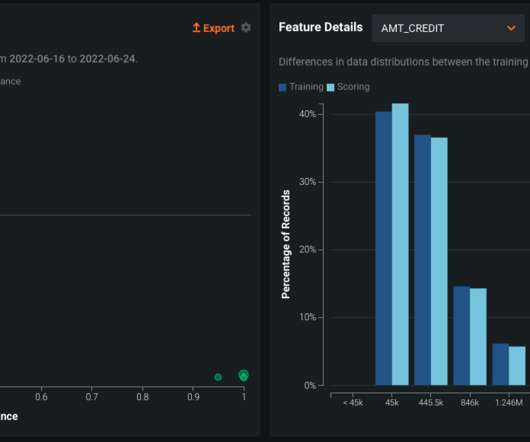
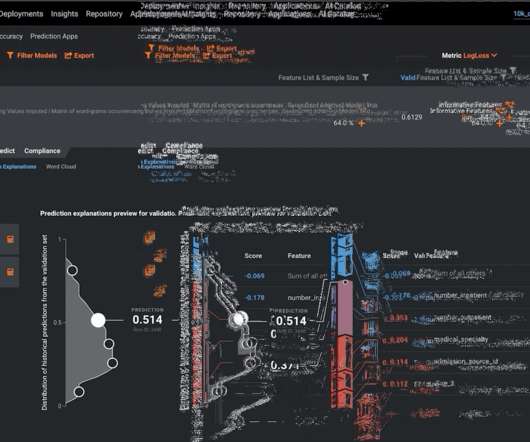
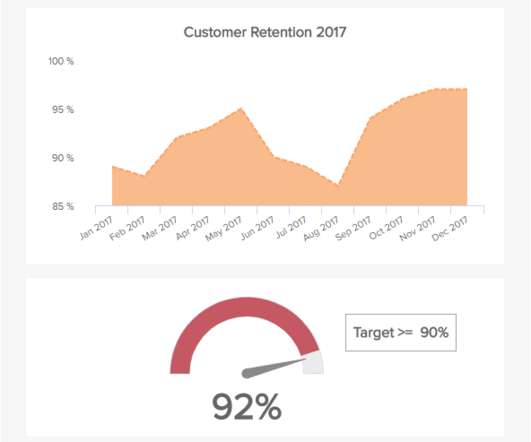
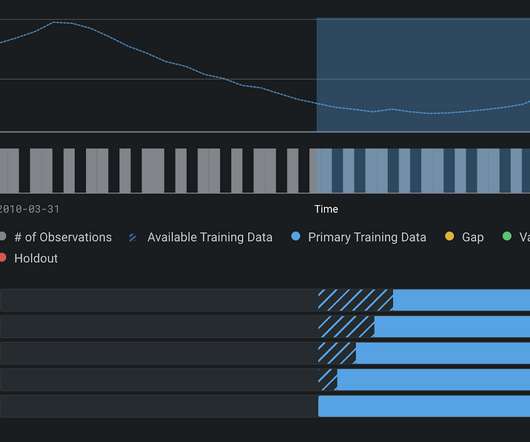
If the assumptions are being breached due to fundamental changes in the process being modeled, the deployed system is not likely to serve its intended purpose, thereby creating further model risk that the institution must manage. These observations would have spanned a distribution, which the model leveraged to make its forecasts.













































Let's personalize your content